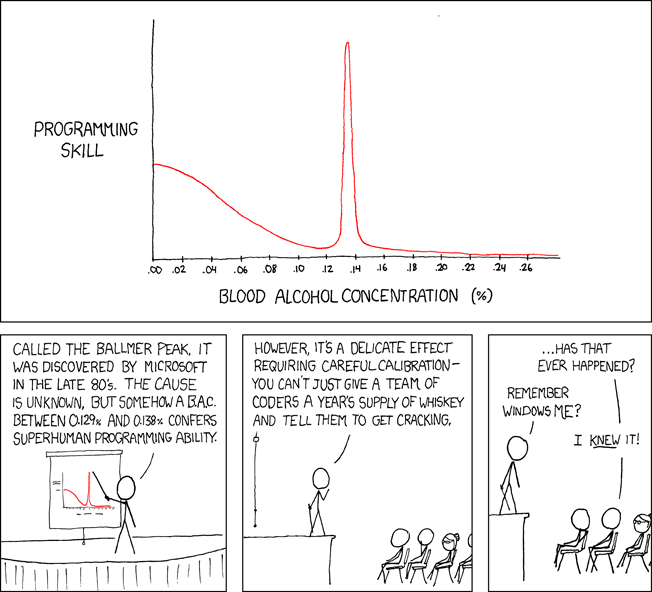
This will be a brief explanation of types of protocols used. Commonly there are three types of protocols which are TCP, UDP and ICMP. TCP is a "connection-oriented protocol" and guaranteed while on the other hand UDP is "connectionless" and not guaranteed.
ICMP uses two types of message types which are Echo Request and Echo Reply.
Servers that accept incoming traffic must be placed on the DMZ network. DMZ stands for "Demilitarized Zone" and keeps incoming traffic secured.
Most of the ports are confined from the firewall side and safe-guard incoming traffic. Ports like 22, 23, 25 can be blocked but there is also a mean on how to redirect traffic.
For example, if port 25 is internally blocked, a sophisticated user can set up a mail server from the outside and send e-mail messages using another different port. In addition, changing to different ports from using the pre-defined ones can prevent hackers to enter your system and this will make the environement ground more safer and secured.
Until next time,
DarkSolo.
Friday, December 26, 2008
Thursday, December 25, 2008
Firewall Explained
In this article, I will teach you how a firewall acts and what it guards within the network environment. So let's get started...
What is a Firewall?
A firewall governs the traffic between at least two networks. Firewalls are commonly altered using UNIX systems but even on Windows platforms, MAC and OS/2 OS's all function well. A well known firewall known as Checkpoint Firewall-1 is a highly secured commercial product and CISCO pix are currently keeping in touch with it.
A Packet Filtering Firewall asks as a filter and not allowing every packet being passed from it without certain settings being set beforehand. A Packet can get accepted, dropped or rejected. When a packet gets accepted, that's not a problem at all. If a packet gets dropped it will take more time to scan for open ports and rejected means it does not accept the packet but sends an ackowledgement back to the sender. The Packet Filtering Firewall oversees five chracteristics in order to accept a packet frame from thr sender which are:
IP of the Destination
Port of the Destination
IP of the Source
Port of the Source
IP Protocol (TCP/UDP)
We can say that a router can act as a firewall and is found at the third Layer of the OSI model which is the Network Layer. Also, certain rules are applied to the firewall to prevent the network from malicious attacks and Denial of Service attacks (DoS attacks).
As an enhancement over the common firewall a newer firewall came to hand called "stateful inspection engine". Basically, it remembers the connection of a conversation between two hosts and only examines the first packet of it.
What is an Application Proxy Firewall?
A packet is sent to the firewall and stopped to be examined and compared to the rules of the router. If they match, the packet is destroyed and re-created into a new data frame. This will make the TCP/IP Protocol Suite much more secured then the Packet Filtering Firewall. The disadvantage is that a Proxy-Application has to be coded for each program. For instance, a Web Application Proxy needs to have a HTTP Proxy, an FTP Application needs to have an FTP Proxy, a Gopher Proxy needs to have a Gopher Proxy etc. The Application Proxy Firewall operates at the seventh Layer of the OSI Model, which is the Applcation Layer.
What is an Application Gateway Firewall?
An Application Gateway Firewall also operates at the seventh Layer and is used to connect to a server from a server before it. Therefore, to telnet to a server and then telnet again from it to another server that is located outside the network.
What is a SOCKS Firewall?
Socks Firewall makes part of the Application Proxy Firewall mentioned earlier. These types of firewalls differ by modified every system in your internal network to communicate with external networks. On Windows or an OS/2 system this can be easily done by swapping some DDL files.
Until next time,
DarkSolo
What is a Firewall?
A firewall governs the traffic between at least two networks. Firewalls are commonly altered using UNIX systems but even on Windows platforms, MAC and OS/2 OS's all function well. A well known firewall known as Checkpoint Firewall-1 is a highly secured commercial product and CISCO pix are currently keeping in touch with it.
A Packet Filtering Firewall asks as a filter and not allowing every packet being passed from it without certain settings being set beforehand. A Packet can get accepted, dropped or rejected. When a packet gets accepted, that's not a problem at all. If a packet gets dropped it will take more time to scan for open ports and rejected means it does not accept the packet but sends an ackowledgement back to the sender. The Packet Filtering Firewall oversees five chracteristics in order to accept a packet frame from thr sender which are:
IP of the Destination
Port of the Destination
IP of the Source
Port of the Source
IP Protocol (TCP/UDP)
We can say that a router can act as a firewall and is found at the third Layer of the OSI model which is the Network Layer. Also, certain rules are applied to the firewall to prevent the network from malicious attacks and Denial of Service attacks (DoS attacks).
As an enhancement over the common firewall a newer firewall came to hand called "stateful inspection engine". Basically, it remembers the connection of a conversation between two hosts and only examines the first packet of it.
What is an Application Proxy Firewall?
A packet is sent to the firewall and stopped to be examined and compared to the rules of the router. If they match, the packet is destroyed and re-created into a new data frame. This will make the TCP/IP Protocol Suite much more secured then the Packet Filtering Firewall. The disadvantage is that a Proxy-Application has to be coded for each program. For instance, a Web Application Proxy needs to have a HTTP Proxy, an FTP Application needs to have an FTP Proxy, a Gopher Proxy needs to have a Gopher Proxy etc. The Application Proxy Firewall operates at the seventh Layer of the OSI Model, which is the Applcation Layer.
What is an Application Gateway Firewall?
An Application Gateway Firewall also operates at the seventh Layer and is used to connect to a server from a server before it. Therefore, to telnet to a server and then telnet again from it to another server that is located outside the network.
What is a SOCKS Firewall?
Socks Firewall makes part of the Application Proxy Firewall mentioned earlier. These types of firewalls differ by modified every system in your internal network to communicate with external networks. On Windows or an OS/2 system this can be easily done by swapping some DDL files.
Until next time,
DarkSolo
Wednesday, December 24, 2008
Doorway Pages Expained
What are Doorway Pages?
Doorway Pages trick the users and by cheating in Search Engines and showing a false wesbite by redirecting visitors to another wesbite. Keywords are stuffed into META tags to take advantage over the other pages in the Search Engine. Doorway Pages are commonly known as Jump Pages, Zebra Pages, Portal Pages, Bridge Pages, Entry Pages, Gateway Pages and others.
In other words, they spamindex the Search Engines. Doorway Pages can be sometimes slow and irritating, taking much loading time and getting the visitor frastrated enough to lose temper and leaves the site. Doorway Pages use some type of cloaking method.
How do Doorway Pages work?
When a visitor types keywords in a Search Engine, it will automatically come up with results related to the keywords typed in by the visitor him/her self. Therefore, they use high ranking keywords to achieve a high ranking in Search Engines and use the META refresh command to fastly redirect the visitor into another website automatically without the user intention to do so.
This is done by using some type of Scripting language such as Javascript which is Client Sided or any Server Sided script such as PHP or Perl that can generate a dynamic webpage everytime a visitor visits the webpage. Redirection can be set either from the .htaccess file or else from the Server Configuration File.
The scope of using a Doorway Page is for the Search Engines and not for the visitors. Somtimes, a doorway page copies another website that already has a high ranking in the Search Engines and steals its identity to portrait a new website and take over it. This is called cloaking.
What is Cloaking?
Cloaking websites have to be Search Engine Friendly (SEF) as by graphical means and also by navigating means or else it will get banned from the index for an undisclosed amount of time. These types of sites can easily be identified by their IP address and/or User Agent whether it's a visitor or a bot. The show a site to the visitor but a different one to the Web Crawler by using Server Side Scripts.
Since the META refresh command can't be used with certain Search Engines and can often fine you with a penalty, Javascript is used, or else by displaying false hyper links with keywords out of scope on the subject and redirected to the site at ease.
What are Content Rich Doorway pages?
Content Rich Doorway pages are more sophisticated doorway pages and make their way to the top in Search Engines without using any means of redirection. In these types of pages, visitors are placed with links to take them to another page. They need to be human-friendly and having a pleasant appearance.
Most of the pages found online are Content Rich Pages and are redirected either to Maximize SEO campaigns or by increasing Pay-Per-Click compaigns.
Until next time,
DarkSolo
Doorway Pages trick the users and by cheating in Search Engines and showing a false wesbite by redirecting visitors to another wesbite. Keywords are stuffed into META tags to take advantage over the other pages in the Search Engine. Doorway Pages are commonly known as Jump Pages, Zebra Pages, Portal Pages, Bridge Pages, Entry Pages, Gateway Pages and others.
In other words, they spamindex the Search Engines. Doorway Pages can be sometimes slow and irritating, taking much loading time and getting the visitor frastrated enough to lose temper and leaves the site. Doorway Pages use some type of cloaking method.
How do Doorway Pages work?
When a visitor types keywords in a Search Engine, it will automatically come up with results related to the keywords typed in by the visitor him/her self. Therefore, they use high ranking keywords to achieve a high ranking in Search Engines and use the META refresh command to fastly redirect the visitor into another website automatically without the user intention to do so.
This is done by using some type of Scripting language such as Javascript which is Client Sided or any Server Sided script such as PHP or Perl that can generate a dynamic webpage everytime a visitor visits the webpage. Redirection can be set either from the .htaccess file or else from the Server Configuration File.
The scope of using a Doorway Page is for the Search Engines and not for the visitors. Somtimes, a doorway page copies another website that already has a high ranking in the Search Engines and steals its identity to portrait a new website and take over it. This is called cloaking.
What is Cloaking?
Cloaking websites have to be Search Engine Friendly (SEF) as by graphical means and also by navigating means or else it will get banned from the index for an undisclosed amount of time. These types of sites can easily be identified by their IP address and/or User Agent whether it's a visitor or a bot. The show a site to the visitor but a different one to the Web Crawler by using Server Side Scripts.
Since the META refresh command can't be used with certain Search Engines and can often fine you with a penalty, Javascript is used, or else by displaying false hyper links with keywords out of scope on the subject and redirected to the site at ease.
What are Content Rich Doorway pages?
Content Rich Doorway pages are more sophisticated doorway pages and make their way to the top in Search Engines without using any means of redirection. In these types of pages, visitors are placed with links to take them to another page. They need to be human-friendly and having a pleasant appearance.
Most of the pages found online are Content Rich Pages and are redirected either to Maximize SEO campaigns or by increasing Pay-Per-Click compaigns.
Until next time,
DarkSolo
Tuesday, December 23, 2008
Port Scanning Explained
<<-- Port Scanning -->>
What is a Port Scanner?
A Port Scanner is an application that scans specific or a range of ports to determine which are open, closed or filtered. We can compare this anology as having a door to each room. Every serivce (application) running on the system has a predefined port number assigned to it. The door will be the port number and the room will be the application. Someone can "portsweep" for multiple hosts and determine which port is listening on a specific service. For example, one can portsweep Port 80 to discover web browsing flaws. A light port scan will make a scan more quickly than a full scan.
Port Scanning can be an illegal action in certain countries. Most system administrators checks the logs as a daily routine to determine whether there has been an attempt. I would suggest that you sign a contract between you and the person you've going to port scan as you don't want to get into trouble.
Ports come in two different flavours: The TCP (Transmission Control Protocol) and UDP (Userdatagram Protocol). TCP can be described as "connection oriented" whilst UDP is "connectionless". They both rely on the protocol stack where today it is commonly known as "TCP/IP" stack.
There are a total of 65536 ports available and are assosiated by the (Internet Assigned Numbers Authority) IANA.
Since UDP is an unreliable port it will require more time to scan than TCP.
Some Port Scanners will just tell you which ports are open and closed whilst others will give you a brief explanation on that port and what type of exploit can be attempted with it.
Apart from that, Port Scanners can determine what Operating System you're using and information about that particular service (port).
Two commonly known Port Scanners are nmap and Nessus which are both open source. Originally nmap was designed to scan larger networks, although even single hosts can be scaned also. Nmap makes use of raw IP packets in novel to conlude which hosts are on the network, what services are being offered, Operating System version, types of packets filters/firewalls and more. Nmap can be downloaded freely and is open source. Both command line and Graphical User Interface (GUI) exist. The open source falls under the agreement of the GNU GPL.
Nessus is also a reliable port scanner and can provide certain amount of valuable information. These two are both the best Port Scanners there are out there nowadays.
If you don't want to install a Port Scanner on your system, one can easily use a Web based Port Scanner to scan a system and draws a picture on how it looks at the other side of the Internet. These Web based Port Scanners scan quickly and provide you with the essential information only.
Google for "Web Based Port Scanner" or "free online Port Scanner" to use one.
Until next time,
DarkSolo
What is a Port Scanner?
A Port Scanner is an application that scans specific or a range of ports to determine which are open, closed or filtered. We can compare this anology as having a door to each room. Every serivce (application) running on the system has a predefined port number assigned to it. The door will be the port number and the room will be the application. Someone can "portsweep" for multiple hosts and determine which port is listening on a specific service. For example, one can portsweep Port 80 to discover web browsing flaws. A light port scan will make a scan more quickly than a full scan.
Port Scanning can be an illegal action in certain countries. Most system administrators checks the logs as a daily routine to determine whether there has been an attempt. I would suggest that you sign a contract between you and the person you've going to port scan as you don't want to get into trouble.
Ports come in two different flavours: The TCP (Transmission Control Protocol) and UDP (Userdatagram Protocol). TCP can be described as "connection oriented" whilst UDP is "connectionless". They both rely on the protocol stack where today it is commonly known as "TCP/IP" stack.
There are a total of 65536 ports available and are assosiated by the (Internet Assigned Numbers Authority) IANA.
Since UDP is an unreliable port it will require more time to scan than TCP.
Some Port Scanners will just tell you which ports are open and closed whilst others will give you a brief explanation on that port and what type of exploit can be attempted with it.
Apart from that, Port Scanners can determine what Operating System you're using and information about that particular service (port).
Two commonly known Port Scanners are nmap and Nessus which are both open source. Originally nmap was designed to scan larger networks, although even single hosts can be scaned also. Nmap makes use of raw IP packets in novel to conlude which hosts are on the network, what services are being offered, Operating System version, types of packets filters/firewalls and more. Nmap can be downloaded freely and is open source. Both command line and Graphical User Interface (GUI) exist. The open source falls under the agreement of the GNU GPL.
Nessus is also a reliable port scanner and can provide certain amount of valuable information. These two are both the best Port Scanners there are out there nowadays.
If you don't want to install a Port Scanner on your system, one can easily use a Web based Port Scanner to scan a system and draws a picture on how it looks at the other side of the Internet. These Web based Port Scanners scan quickly and provide you with the essential information only.
Google for "Web Based Port Scanner" or "free online Port Scanner" to use one.
Until next time,
DarkSolo
Sunday, December 21, 2008
IP Address Explanation
<<-- IP Address Explained -->>
In this article, I will be demonstrating how an IP address is assembled. Each machine connected to the Internet has an unique number in order to identity the host, hence this is called an "IP Address". An IP address looks like the one shown below:
216.27.61.137
An IP address normally takes the form of decimal format "dotted decimal number" rather than a binary form. Though computers need to make use of binary form since it can only understand that. The binary form shown below is the same as the IP address written above:
11011000.00011011.00111101.10001001
Each eight bits found in the IP address above is called an "octet". If you add all the four digit numbers together you'll end up with 32, therefore IP addresses are considered to be 32-bit. IN this scenario we are talking about IPv4 addresses. You can have two diffrent states (1 or 0) for every eight bits and therefore written as 2^8 or 256 per octet. Therefore, each octet can have a value between 0 and 255 (since 0 is included also). Combining the four octets and you end up with 2^32 or 4,294,967,296 values which are unique!
As one can see, there is a possible combination of nearly 4.3 billion. Most of these IP address are reserved and can't be used such as the IP address 0.0.0.0 is reserved for the default network and 255.255.255.255 is reserved for broadcasts.
IP addresses are grouped into classes and therefore octets help make this simpler. With this being used, you can split IP address with their own department. Octets are split into two sections: the Net and Host.
The Net is always the first octet and it determines the network a host belongs to. On the other hand, the host, also referred to as Node/Machine determines the computer on the network. The host sections always contains the last octet.
IP addresses are grouped into five different IP classes.
Default Network - The IP address of 0.0.0.0 is used for the default network.
Loopback - The IP address 127.0.0.1 is considered to be the "loopback address" and it's use is it configure your own settings by sending a message to yourself. It is nomrally used to troubleshoot and test your own network (NIC Card).
IP Address Classes
Class A Range 1 - 127 (Reserved for loopback and internal testing)
Net Host or Node
115. 24.53.107
Class B Range 128 - 191
Class C Range 192 - 223
Class D Range 224 - 239 (Reserved for multicast)
Class E Range 240 - 255 (Reserved for experimentation, used for research)
Private Address Space
Class A
10.0.0.0 to 10.255.255.255
Class B
172.16.0.0. to 172.32.255.255
Class C
192.168.0.0 to 192.168.255.255
Default Subnet Masks
Class A
255.0.0.0
Class B
255.255.0.0
Class C
255.255.255.0
Until next time,
DarkSolo
In this article, I will be demonstrating how an IP address is assembled. Each machine connected to the Internet has an unique number in order to identity the host, hence this is called an "IP Address". An IP address looks like the one shown below:
216.27.61.137
An IP address normally takes the form of decimal format "dotted decimal number" rather than a binary form. Though computers need to make use of binary form since it can only understand that. The binary form shown below is the same as the IP address written above:
11011000.00011011.00111101.10001001
Each eight bits found in the IP address above is called an "octet". If you add all the four digit numbers together you'll end up with 32, therefore IP addresses are considered to be 32-bit. IN this scenario we are talking about IPv4 addresses. You can have two diffrent states (1 or 0) for every eight bits and therefore written as 2^8 or 256 per octet. Therefore, each octet can have a value between 0 and 255 (since 0 is included also). Combining the four octets and you end up with 2^32 or 4,294,967,296 values which are unique!
As one can see, there is a possible combination of nearly 4.3 billion. Most of these IP address are reserved and can't be used such as the IP address 0.0.0.0 is reserved for the default network and 255.255.255.255 is reserved for broadcasts.
IP addresses are grouped into classes and therefore octets help make this simpler. With this being used, you can split IP address with their own department. Octets are split into two sections: the Net and Host.
The Net is always the first octet and it determines the network a host belongs to. On the other hand, the host, also referred to as Node/Machine determines the computer on the network. The host sections always contains the last octet.
IP addresses are grouped into five different IP classes.
Default Network - The IP address of 0.0.0.0 is used for the default network.
Loopback - The IP address 127.0.0.1 is considered to be the "loopback address" and it's use is it configure your own settings by sending a message to yourself. It is nomrally used to troubleshoot and test your own network (NIC Card).
IP Address Classes
Class A Range 1 - 127 (Reserved for loopback and internal testing)
Net Host or Node
115. 24.53.107
Class B Range 128 - 191
Class C Range 192 - 223
Class D Range 224 - 239 (Reserved for multicast)
Class E Range 240 - 255 (Reserved for experimentation, used for research)
Private Address Space
Class A
10.0.0.0 to 10.255.255.255
Class B
172.16.0.0. to 172.32.255.255
Class C
192.168.0.0 to 192.168.255.255
Default Subnet Masks
Class A
255.0.0.0
Class B
255.255.0.0
Class C
255.255.255.0
Until next time,
DarkSolo
NetBIOS Exploit Explained
<<-- NetBIOS Attack -->>
Part 1
NetBIOS which stands for "Network Basic Input Output System" allows other nodes on a network to send data to each other over a LAN (Local Area Network). It was released by IBM and later on Microsoft starting adapting it for it's own Operating System. Modern OS's are having NetBIOS Extended User Interface (NetBEUI) installed with them but in order to communicate over a WAN (Wide Are Network) you need to user another type of protocol such as TCP (Transmission Control Protocol) rather than NetBIOS.
When you request from NetBIOS it takes the form of a Network Control Block (NCB) that specifies a message location and a name of the destination.
NetBIOS makes use of the session and transport layers that are found in the OSI (Open Systems Interconnection) model. Though it does not provide a standard frame or frame format for data transmission. NetBEUI takes care in order to capsulate a standard frame.
The communication nodes found in NetBIOS are session or datagram. Session mode provides two nodes on the network to talk with each other and therefore creates a "session". It can handle bulky messages and takes care of error detection and recovery. On the other hand, Datagram mode is "connectionless" which means it uses UDP and the data being transmitted is not guaranteed that it will arrive to the destination. Therefore, the messages must be smaller, sent independently and is also responsible for error detection and recovery. Datagram mode can also send a broadcast message to all the machines connected on the LAN.
Part 2
In this tutorial we will be demonstrating one of the easiest ways hackers manage to gain access to your network infrastructure within minutes. I certainly most of all condemn the acts of a hacker but not opposed of an ethical hacker, one that has to works with the network administrators and aware them to path their systems for leaks and holes.
If you skimmed through Part 1, I strongly recommend that you go back and read that one first to get an idea of what NetBIOS really is. I'll continue stretching my explanation in this tutorial and I'll introduce a new exploit found in the Windows Operating System itself called the "NetBIOS Attack".
NetBIOS was developed by IBM and Sytek as an API (Application Programming Interface) for clients to share information over a LAN (Local Area Network). This commonly works on Windows 9x platforms such as Windows98, Windows Me, Windows NT etc.
Having that said, I have no doubt that you've must have clicked on the "Network Neighborhood" in order to access other nodes on the network. Do you know what happens you tend to click on it? Your machine requests the names of the computers connected to the network (LAN) in combination with NetBIOS. So what NetBIOS actually does is, it gives the names and general information of computers attached to the network. Such information includes:
Name of the Machine
User Name
Domain
Host Name
These are the most vital information that we need. Like any other service, each runs a specific port number, in this case NetBIOS runs either on 139 or 445.
Using the NBTSTAT Command
This is the command found in MSDOS in order to communicate with the NetBIOS. Once you have launched command prompt you will end up with this:
c:\ or c:\windows>
If you get something else written after the C:\ don't worry, just keep reading. It will still work. So, we want to get information about victim's machine so therefore we type the command:
c:\windows>nbtstat -a 255.255.255.255
255.255.255.255 will be used as an example. You end up with the following information about the victim's machine.
NetBIOS Remote Machine Name Table
Name Number Type Usage
==========================================================================
workgroup 00 G Domain Name
my_computer 03 U Messenger Service
myusername 03 U Messenger Service
MAC Address = 00-02-44-14-23-E6
We have the MAC address, we might make use of that piece of information later on. It's written as a string of hexadecimal numbers.
Now, we have the name of NetBIOS session and the type of service it is running.
Types of Attacks
There are two types of attacks that can launched using NetBIOS such as:
1. Reading/Writing to a remote machine
2.Denial of Service (DoS) Attack
To search for a victim we need a port scanner which will aware us what type of Operating System and Services the victim is currently running. A port scanner will scan a given range to track down open ports on the system. A commonly notorious port scanner is "Orge" that will give out NetBIOS names of the remote machine.
You can also download an application called "nbtscan" from http://www.unixwiz.net/tools/nbtscan.html and it will provide you with open netBIOS nameservers.
Believe it or not, as stated already NetBIOS is one of the easiest hack there is. Though, it works with luck. The victim needs to hack "File and Sharing" enabled in order to take revenge over his or her machine.
Now let's suppose that we type:
c:\windows>nbtstat -a 255.255.255.255 and the following table turns up:
NetBIOS Remote Machine Name Table
Name Type Status
------------------------------------------------------------------------------------------------- user <00> UNIQUE Registered workgroup <00> GROUP Registered user <03> UNIQUE Registered user <20> UNIQUE Registered
MAC Address = 00-02-44-14-23-E6
Bingo! The number <20> indicates as a number that the victim has enabled the "File and Printer Sharing" feature.
Note: If <20> doesn't show up, we can conclude that "File and Printer Sharing" is not enabled or if you are prompt with an error message saying "Host Not Found" then port 139 is closed, blocked by some type of firwall or the IP address doesn't exists.
We are nearly up the hill. Now, we need to know what type of files and folders/printers are being shared on the LAN network. There we use the following command:
c:\windows>net view \\255.255.255.255
Let suppose we get the following output
Shared resources at \\255.255.255.255 ComputerNameGoesHere
Share name Type Used as Comment
----------------------------------------------------------------------------------------------- CDISK Disk
The command completed successfully.
Here we know that we have a type of mechanism which is a Disk and assigned with a share name CDISK. To get further information we'll type:
Shared resources at \\255.255.255.255
ComputerNameGoesHere
Share name Type Used as Comment
----------------------------------------------------------------------------------------------- HP-15 Print
Here we know that the Victim has a Printer installed with the sharename Hp-15.
Let's say that the victim has a shared Printer. That's already a huge advantage, since we can print paper remotely without him noticing.
Now that we are equipped with the IP address of the victim, File and Printer Sharing is confirmed enabled and the victim's hard disk's name is CDISK the last step is to connect to it and seek more files and folders.
Therefore, we introduce the NET command.
Let's say that we want our new drive letter to be assigned as x: we can connect using this command:
C:\windows\net use x: \\255.255.255.255\CDISK
Note: X may be replaced with another other letter.
If everything goes well you will finally receive the message: "The command was completed successfully" .
Now all you have to do is double click on "My Computer" and VIOLA!!!
All files and Folders are accessible.
You can alter the files only if you have a certain degree of permissions enabled. You have just created a new drive x: on your computer. You can now enter the victim's hard drive anytime you like, as long you're still remotely connected to it.
<<-- Further Explanation -->>
There are cases where you try and connect to the victim's computer and you are requested for password. It's commonly set as "Administrator" though most of the time they change it to something else. There is a program which will do all the dirty work for you called "PQWAK". All it requires is the IP address and the Sharename of the host and it will decrypt the password hash within seconds.
Note: Passwords will only be cracked if the victim is running one of the following OS's;
Windows 95
Windows 98
Windows Me
<<-- The IPC$ Hidden Share Hack found in Windows NT, 2000, XP -->>
This is used in case the password isn't crackable. It will gain access to the victim's machine just by typing a single string command which will log in as a guest and not act as a password cracker itself. So, it's:
c:\windows\net use x: \\255.255.255.255\ipc$ "" /user:""
This will now actually gain access rights as the one explained above but it will prove useful information such as shared drives, names of user names, users that never logged in etc. Two tools that use this type of method are "Internet Periscope" and "enum" which is basically command line.
If you're lucky enough and have write access permissions you can place files on the hard drive such as keyloggers, trojans etc which will later on open further holes in the OS if the victim is lame enough to double click on the executable files and start the service.
<<-- How to Protect yourself from such an attack -->>
Visit the Microsoft Update's page and let the updates install automatically -
http://windowsupdate.microsoft.com
That's all for now, until then,
DarkSolo
Part 1
NetBIOS which stands for "Network Basic Input Output System" allows other nodes on a network to send data to each other over a LAN (Local Area Network). It was released by IBM and later on Microsoft starting adapting it for it's own Operating System. Modern OS's are having NetBIOS Extended User Interface (NetBEUI) installed with them but in order to communicate over a WAN (Wide Are Network) you need to user another type of protocol such as TCP (Transmission Control Protocol) rather than NetBIOS.
When you request from NetBIOS it takes the form of a Network Control Block (NCB) that specifies a message location and a name of the destination.
NetBIOS makes use of the session and transport layers that are found in the OSI (Open Systems Interconnection) model. Though it does not provide a standard frame or frame format for data transmission. NetBEUI takes care in order to capsulate a standard frame.
The communication nodes found in NetBIOS are session or datagram. Session mode provides two nodes on the network to talk with each other and therefore creates a "session". It can handle bulky messages and takes care of error detection and recovery. On the other hand, Datagram mode is "connectionless" which means it uses UDP and the data being transmitted is not guaranteed that it will arrive to the destination. Therefore, the messages must be smaller, sent independently and is also responsible for error detection and recovery. Datagram mode can also send a broadcast message to all the machines connected on the LAN.
Part 2
In this tutorial we will be demonstrating one of the easiest ways hackers manage to gain access to your network infrastructure within minutes. I certainly most of all condemn the acts of a hacker but not opposed of an ethical hacker, one that has to works with the network administrators and aware them to path their systems for leaks and holes.
If you skimmed through Part 1, I strongly recommend that you go back and read that one first to get an idea of what NetBIOS really is. I'll continue stretching my explanation in this tutorial and I'll introduce a new exploit found in the Windows Operating System itself called the "NetBIOS Attack".
NetBIOS was developed by IBM and Sytek as an API (Application Programming Interface) for clients to share information over a LAN (Local Area Network). This commonly works on Windows 9x platforms such as Windows98, Windows Me, Windows NT etc.
Having that said, I have no doubt that you've must have clicked on the "Network Neighborhood" in order to access other nodes on the network. Do you know what happens you tend to click on it? Your machine requests the names of the computers connected to the network (LAN) in combination with NetBIOS. So what NetBIOS actually does is, it gives the names and general information of computers attached to the network. Such information includes:
Name of the Machine
User Name
Domain
Host Name
These are the most vital information that we need. Like any other service, each runs a specific port number, in this case NetBIOS runs either on 139 or 445.
Using the NBTSTAT Command
This is the command found in MSDOS in order to communicate with the NetBIOS. Once you have launched command prompt you will end up with this:
c:\ or c:\windows>
If you get something else written after the C:\ don't worry, just keep reading. It will still work. So, we want to get information about victim's machine so therefore we type the command:
c:\windows>nbtstat -a 255.255.255.255
255.255.255.255 will be used as an example. You end up with the following information about the victim's machine.
NetBIOS Remote Machine Name Table
Name Number Type Usage
==========================================================================
workgroup 00 G Domain Name
my_computer 03 U Messenger Service
myusername 03 U Messenger Service
MAC Address = 00-02-44-14-23-E6
We have the MAC address, we might make use of that piece of information later on. It's written as a string of hexadecimal numbers.
Now, we have the name of NetBIOS session and the type of service it is running.
Types of Attacks
There are two types of attacks that can launched using NetBIOS such as:
1. Reading/Writing to a remote machine
2.Denial of Service (DoS) Attack
To search for a victim we need a port scanner which will aware us what type of Operating System and Services the victim is currently running. A port scanner will scan a given range to track down open ports on the system. A commonly notorious port scanner is "Orge" that will give out NetBIOS names of the remote machine.
You can also download an application called "nbtscan" from http://www.unixwiz.net/tools/nbtscan.html and it will provide you with open netBIOS nameservers.
Believe it or not, as stated already NetBIOS is one of the easiest hack there is. Though, it works with luck. The victim needs to hack "File and Sharing" enabled in order to take revenge over his or her machine.
Now let's suppose that we type:
c:\windows>nbtstat -a 255.255.255.255 and the following table turns up:
NetBIOS Remote Machine Name Table
Name Type Status
------------------------------------------------------------------------------------------------- user <00> UNIQUE Registered workgroup <00> GROUP Registered user <03> UNIQUE Registered user <20> UNIQUE Registered
MAC Address = 00-02-44-14-23-E6
Bingo! The number <20> indicates as a number that the victim has enabled the "File and Printer Sharing" feature.
Note: If <20> doesn't show up, we can conclude that "File and Printer Sharing" is not enabled or if you are prompt with an error message saying "Host Not Found" then port 139 is closed, blocked by some type of firwall or the IP address doesn't exists.
We are nearly up the hill. Now, we need to know what type of files and folders/printers are being shared on the LAN network. There we use the following command:
c:\windows>net view \\255.255.255.255
Let suppose we get the following output
Shared resources at \\255.255.255.255 ComputerNameGoesHere
Share name Type Used as Comment
----------------------------------------------------------------------------------------------- CDISK Disk
The command completed successfully.
Here we know that we have a type of mechanism which is a Disk and assigned with a share name CDISK. To get further information we'll type:
Shared resources at \\255.255.255.255
ComputerNameGoesHere
Share name Type Used as Comment
----------------------------------------------------------------------------------------------- HP-15 Print
Here we know that the Victim has a Printer installed with the sharename Hp-15.
Let's say that the victim has a shared Printer. That's already a huge advantage, since we can print paper remotely without him noticing.
Now that we are equipped with the IP address of the victim, File and Printer Sharing is confirmed enabled and the victim's hard disk's name is CDISK the last step is to connect to it and seek more files and folders.
Therefore, we introduce the NET command.
Let's say that we want our new drive letter to be assigned as x: we can connect using this command:
C:\windows\net use x: \\255.255.255.255\CDISK
Note: X may be replaced with another other letter.
If everything goes well you will finally receive the message: "The command was completed successfully" .
Now all you have to do is double click on "My Computer" and VIOLA!!!
All files and Folders are accessible.
You can alter the files only if you have a certain degree of permissions enabled. You have just created a new drive x: on your computer. You can now enter the victim's hard drive anytime you like, as long you're still remotely connected to it.
<<-- Further Explanation -->>
There are cases where you try and connect to the victim's computer and you are requested for password. It's commonly set as "Administrator" though most of the time they change it to something else. There is a program which will do all the dirty work for you called "PQWAK". All it requires is the IP address and the Sharename of the host and it will decrypt the password hash within seconds.
Note: Passwords will only be cracked if the victim is running one of the following OS's;
Windows 95
Windows 98
Windows Me
<<-- The IPC$ Hidden Share Hack found in Windows NT, 2000, XP -->>
This is used in case the password isn't crackable. It will gain access to the victim's machine just by typing a single string command which will log in as a guest and not act as a password cracker itself. So, it's:
c:\windows\net use x: \\255.255.255.255\ipc$ "" /user:""
This will now actually gain access rights as the one explained above but it will prove useful information such as shared drives, names of user names, users that never logged in etc. Two tools that use this type of method are "Internet Periscope" and "enum" which is basically command line.
If you're lucky enough and have write access permissions you can place files on the hard drive such as keyloggers, trojans etc which will later on open further holes in the OS if the victim is lame enough to double click on the executable files and start the service.
<<-- How to Protect yourself from such an attack -->>
Visit the Microsoft Update's page and let the updates install automatically -
http://windowsupdate.microsoft.com
That's all for now, until then,
DarkSolo
How to get FREE Internet in the UK
Note: Use this information at your own risk. If you have credit in your mobile phone it will start getting dry so I'll suggest that you use a SIM card without any credit in it.
In this tutorial, I will be demonstrating how to get FREE Internet in case you're a civilian living in the United Kingdom. To get started you'll need the following prerequisites:
A Mobile Phone that is unlocked
An O2 sim card
Proxifier (PC software)
This guide! :)
Ok, so let's get started.
Connect your PC or laptop to your Mobile (bluetooth, IR or Cable).
Most of the time, latest mobile trends come with the manufacturer software on disk such as the following (Motorola phone tools/Nokia PC suite etc).
Then go into the Internet settings of your software, the one you are using as mentioned above and make a new connection using the following settings:
Use these settings:
Access Point- payandgo.o2.co.uk
Username- payandgo
Password- password
Open Proxifier Software
Go to Options/Proxy Settings/Add
Server Address 193.113.200.195 Port 8080
Protocol https
No other settings are required, click OK.
That's it! You are now connected and able to the surf the Internet for FREE via GPRS technology.
Until next time,
DarkSolo
In this tutorial, I will be demonstrating how to get FREE Internet in case you're a civilian living in the United Kingdom. To get started you'll need the following prerequisites:
A Mobile Phone that is unlocked
An O2 sim card
Proxifier (PC software)
This guide! :)
Ok, so let's get started.
Connect your PC or laptop to your Mobile (bluetooth, IR or Cable).
Most of the time, latest mobile trends come with the manufacturer software on disk such as the following (Motorola phone tools/Nokia PC suite etc).
Then go into the Internet settings of your software, the one you are using as mentioned above and make a new connection using the following settings:
Use these settings:
Access Point- payandgo.o2.co.uk
Username- payandgo
Password- password
Open Proxifier Software
Go to Options/Proxy Settings/Add
Server Address 193.113.200.195 Port 8080
Protocol https
No other settings are required, click OK.
That's it! You are now connected and able to the surf the Internet for FREE via GPRS technology.
Until next time,
DarkSolo
Saturday, December 20, 2008
C++ basics
C++ tutorial: Part 1
1: The IDE
With this article, I am hopefully beginning a series of C++ tutorials for complete beginners.
Before you start you will need an IDE (Integrated Development Environment), or alternatively just a text editor and a compiler. An IDE is just a text editor with built-in compiler and debugger.
What is a compiler? A compiler is a program that translates your C++ code into binary instructions that the processor can work with. Ideally we would just tell the computer what to do, and it would obey. But this isn't so easy, since humans are not computers, and computers are not humans. Therefore there is a language barrier, and programming languages try to bridge the gap with a compiler (translator). To be really specific about it, your program doesn't end up as pure cpu instruction, but is laid out in a file format that your operator can help the processor execute.
This is the reason a windows program doesn't work natively on linux, and vice versa.
For IDE I would recommend Dev-Cpp from www.bloodshed.net or Code::Blocks. There are also full-fledged professional development environments for professionals, such as Microsoft Visual Studio (MSVS for short) which costs money, and its little sister, Microsoft Visual C++ Express.
There are free Express editions available for every language supported by Visual Studio, so if you want to get used to an environment that excels at building applications for Microsoft Windows this is probably where you want to go.
Personally, I don't like using msvs for several reasons:
* It's not portable (you can only build programs for windows with it)
* It's bloated (takes a while to load)
* The menu system is too advanced for my feeble mind
In short, I like my IDE light-weight and portable. This is why I don't really use an IDE at all.
So, what do I use? Well, since I want it light-weight, I use a small text editor and a command-line compiler. Don't fear; after developing a few command-line programs you will lose the fear of operating such utilities. Since my main Operating System (OS) is Windows, I use MinGW, which is a Windows port of GNU's compiler collection. The way I've installed this myself is by installing Dev-Cpp and pointing my systems "PATH" environment variable to the bin directory of the compiler (see picture that I will add later, please remind me!).
This allows me to open a command prompt, navigate to my code, and write
c++ -o name codefile.cpp
Yes, this is as easy as it looks. c++ is the name of the program, the -o switch allows you to specify a name for the compiled file, and that's that. If you don't specify a name with -o, the compiled file ends up as a.exe.
Set up your favorite IDE, and let's get coding!
2: Hello World!
Our first program:
#include <iostream>
using std::cout;
int main()
{
// This is a comment and is ignored by the compiler
cout << "Hello, world!\n";
return 0;
}
This prints "Hello, world!" to the screen, with a newline on the end.
"\n" is a newline character, changing line like enter would in notepad.
VERY IMPORTANT: Every "statement" (command) ends with a semicolon (;).
Let's go through it from the top:
#include <iostream>
When the compiler encounters an #include line, it searches its folders for a file of the name between the brackets (greater-than and less-than signs), and if found the line is replaced by the contents of the file. In this case, iostream defines stuff we use later in the code, such as cout.
using std::cout;
This has to do with namespaces which is an advanced topic, but basically it tells the compiler that we don't want to write std:: in front of cout for every time we use it. Std stands for standard, meaning this is a functionality of the C++ standard library (stl). You can also write
using namespace std;
if you use a lot of stuff from the stl.
So, you've already learned an operator! More about that later, but you probably know a few more from before.
int main()
This is a function declaration. A function is a shortcut to a functionality of your program. The main function in any C++ program is the "entry point", that is, when the program is run, it starts from the first line inside main.
Inside? That is what we use the { and the } for. These curly braces are known as a "scope". The function ends when its scope ends.
Moving on to the line prefixed with //, this is a comment and will not be looked at when the compiler tries to translate your code to instructions.
Next up, cout:
This is where all the magic happens. Remember that file we included? It defines a function called cout which is short for console output. So whatever you "shift left" into it is written to the screen. return 0;
To tell you what this line does I think it's about time to tell you about data types and variables.
3: Variables
So, we are making a little program, and we are using cout's evil twin called cin (you guessed it, console input) to get a value from the user. Here is the program:
#include <iostream>
#include <string>
using namespace std;
int main()
{
string name;
cout << "Please enter your name: ";
cin >> name;
cout << "Hello, " << name << "\n";
return 0;
}
This program asks for your name and greets you with it. To be able to do this, we have to store your name temporarily. So we put it into a little box called a variable, and write "name" on the lid of the box. So when we want to use the name again we just refer to this box instead.
Let's talk about data. Data can be of several types. To the computer all data is just binary numbers, but this would make it hard to work with for humans. So when programming, we categorize our data into different datatypes:
On the numeric types you can specify it being signed or unsigned, signed meaning it can be negative.
In addition there are other types such as string, that are not standard C++ (see we included <string> up there?)
So in our function declaration
int main()
we specify that main is a function of type integer. This means that it returns an int.
So after the program runs, it returns a 0 to the operating system (which "called" it to start the program). Operating systems use integer return values to determine if a program executed properly. This comes in handy to check for errors later.
So, let's get to those pesky operators next...
4: Operators
You probably know a few of the operators from before. Here they are:
The modulo operator is quite useful if you have a random number and want it to be within a certain range.
For example, we have 300 and want it to be a number from 0 to 24. If you were to count to 300, but resetting to 0 every time you reached 24, you would end up at 300 % 24 which is 12.
The logic operators come in handy when you use conditionals.
5: Conditionals
if (this is true) { then do this } else { if not, do this }
This should be pretty self explanatory. To illustrate how a boolean works,
bool b = true;
if (b)
{
cout << "b is true";
} else
{
cout << "b is false";
}
While is also pretty self explanatory if you know english.
while (b) { if (1 != 1) { break; } }
This is a "while loop". While the condition is true, it executes what's in the braces. Break exits the loop. Try to guess what this one does.
Another type of loop is called "for":
for (int i = 10; ++i);
Here you declare a variable, then set the condition, then set what to do for each time the loop is finished running through.
All except for the condition are optional and you can leave them blank if you so desire.
Now let's declare our own function:
int multiply(int x, int y)
{
return x * y;
}
What this does should be fairly understandable if you made it this far. It multiplies its two inputs and returns the value. In other words, it returns the product of its inputs.
That's it for now. My tutorial basically sucks compared to learncpp.com, so you should check that out
until next time. :)
- h3x
1: The IDE
With this article, I am hopefully beginning a series of C++ tutorials for complete beginners.
Before you start you will need an IDE (Integrated Development Environment), or alternatively just a text editor and a compiler. An IDE is just a text editor with built-in compiler and debugger.
What is a compiler? A compiler is a program that translates your C++ code into binary instructions that the processor can work with. Ideally we would just tell the computer what to do, and it would obey. But this isn't so easy, since humans are not computers, and computers are not humans. Therefore there is a language barrier, and programming languages try to bridge the gap with a compiler (translator). To be really specific about it, your program doesn't end up as pure cpu instruction, but is laid out in a file format that your operator can help the processor execute.
This is the reason a windows program doesn't work natively on linux, and vice versa.
For IDE I would recommend Dev-Cpp from www.bloodshed.net or Code::Blocks. There are also full-fledged professional development environments for professionals, such as Microsoft Visual Studio (MSVS for short) which costs money, and its little sister, Microsoft Visual C++ Express.
There are free Express editions available for every language supported by Visual Studio, so if you want to get used to an environment that excels at building applications for Microsoft Windows this is probably where you want to go.
Personally, I don't like using msvs for several reasons:
* It's not portable (you can only build programs for windows with it)
* It's bloated (takes a while to load)
* The menu system is too advanced for my feeble mind
In short, I like my IDE light-weight and portable. This is why I don't really use an IDE at all.
So, what do I use? Well, since I want it light-weight, I use a small text editor and a command-line compiler. Don't fear; after developing a few command-line programs you will lose the fear of operating such utilities. Since my main Operating System (OS) is Windows, I use MinGW, which is a Windows port of GNU's compiler collection. The way I've installed this myself is by installing Dev-Cpp and pointing my systems "PATH" environment variable to the bin directory of the compiler (see picture that I will add later, please remind me!).
This allows me to open a command prompt, navigate to my code, and write
c++ -o name codefile.cpp
Yes, this is as easy as it looks. c++ is the name of the program, the -o switch allows you to specify a name for the compiled file, and that's that. If you don't specify a name with -o, the compiled file ends up as a.exe.
Set up your favorite IDE, and let's get coding!
2: Hello World!
Our first program:
#include <iostream>
using std::cout;
int main()
{
// This is a comment and is ignored by the compiler
cout << "Hello, world!\n";
return 0;
}
This prints "Hello, world!" to the screen, with a newline on the end.
"\n" is a newline character, changing line like enter would in notepad.
VERY IMPORTANT: Every "statement" (command) ends with a semicolon (;).
Let's go through it from the top:
#include <iostream>
When the compiler encounters an #include line, it searches its folders for a file of the name between the brackets (greater-than and less-than signs), and if found the line is replaced by the contents of the file. In this case, iostream defines stuff we use later in the code, such as cout.
using std::cout;
This has to do with namespaces which is an advanced topic, but basically it tells the compiler that we don't want to write std:: in front of cout for every time we use it. Std stands for standard, meaning this is a functionality of the C++ standard library (stl). You can also write
using namespace std;
if you use a lot of stuff from the stl.
So, you've already learned an operator! More about that later, but you probably know a few more from before.
int main()
This is a function declaration. A function is a shortcut to a functionality of your program. The main function in any C++ program is the "entry point", that is, when the program is run, it starts from the first line inside main.
Inside? That is what we use the { and the } for. These curly braces are known as a "scope". The function ends when its scope ends.
Moving on to the line prefixed with //, this is a comment and will not be looked at when the compiler tries to translate your code to instructions.
Next up, cout:
This is where all the magic happens. Remember that file we included? It defines a function called cout which is short for console output. So whatever you "shift left" into it is written to the screen. return 0;
To tell you what this line does I think it's about time to tell you about data types and variables.
3: Variables
So, we are making a little program, and we are using cout's evil twin called cin (you guessed it, console input) to get a value from the user. Here is the program:
#include <iostream>
#include <string>
using namespace std;
int main()
{
string name;
cout << "Please enter your name: ";
cin >> name;
cout << "Hello, " << name << "\n";
return 0;
}
This program asks for your name and greets you with it. To be able to do this, we have to store your name temporarily. So we put it into a little box called a variable, and write "name" on the lid of the box. So when we want to use the name again we just refer to this box instead.
Let's talk about data. Data can be of several types. To the computer all data is just binary numbers, but this would make it hard to work with for humans. So when programming, we categorize our data into different datatypes:
| int (integer) | these are whole numbers (and take up 4 bytes) |
| char (character) | These are characters, including letters, numbers and symbols. (takes up 1 byte) |
| bool (boolean) | Can be either true or false (takes up 1 byte) |
| float (floating point number) | A number with a decimal comma somewhere in it |
| long (long int) | Can store a greater range of values than a regular int |
| double | Twice the precision of a float |
| short (short int) | Ideal for small numbers if you're concerned about memory use (2 bytes) |
| void | This is used in special cases when no data is used |
On the numeric types you can specify it being signed or unsigned, signed meaning it can be negative.
In addition there are other types such as string, that are not standard C++ (see we included <string> up there?)
So in our function declaration
int main()
we specify that main is a function of type integer. This means that it returns an int.
So after the program runs, it returns a 0 to the operating system (which "called" it to start the program). Operating systems use integer return values to determine if a program executed properly. This comes in handy to check for errors later.
So, let's get to those pesky operators next...
4: Operators
You probably know a few of the operators from before. Here they are:
| + | plus |
| - | minus |
| * | multiplication |
| / | division |
| % | modulo |
| << | shift left |
| >> | shift right |
| && | logic AND |
| || | logic OR |
| ! | logic NOT |
| == | equality |
| != | inequality |
| = | assignment |
| ++ | increment (+1) |
| -- | decrement (-1) |
The modulo operator is quite useful if you have a random number and want it to be within a certain range.
For example, we have 300 and want it to be a number from 0 to 24. If you were to count to 300, but resetting to 0 every time you reached 24, you would end up at 300 % 24 which is 12.
The logic operators come in handy when you use conditionals.
5: Conditionals
if (this is true) { then do this } else { if not, do this }
This should be pretty self explanatory. To illustrate how a boolean works,
bool b = true;
if (b)
{
cout << "b is true";
} else
{
cout << "b is false";
}
While is also pretty self explanatory if you know english.
while (b) { if (1 != 1) { break; } }
This is a "while loop". While the condition is true, it executes what's in the braces. Break exits the loop. Try to guess what this one does.
Another type of loop is called "for":
for (int i = 10; ++i);
Here you declare a variable, then set the condition, then set what to do for each time the loop is finished running through.
All except for the condition are optional and you can leave them blank if you so desire.
Now let's declare our own function:
int multiply(int x, int y)
{
return x * y;
}
What this does should be fairly understandable if you made it this far. It multiplies its two inputs and returns the value. In other words, it returns the product of its inputs.
That's it for now. My tutorial basically sucks compared to learncpp.com, so you should check that out
until next time. :)
- h3x
Windows 2000 Source Code
/* Source Code Windows 2000 */
#include "win31.h"
#include "win95.h"
#include "win98.h"
#include "workst~1.h"
#include "evenmore.h"
#include "oldstuff.h"
#include "billrulz.h"
#include "monopoly.h"
#include "backdoor.h"
#define INSTALL = HARD
char make_prog_look_big(16000000);
void main()
{
* while(!CRASHED)
* {
*** display_copyright_message();
*** display_bill_rules_message();
*** do_nothing_loop();
*** if (first_time_installation)
***** {
***** make_100_megabyte_swapfile();
***** do_nothing_loop();
***** totally_screw_up_HPFS_file_system();
***** search_and_destroy_the_rest_of-OS2();
***** make_futile_attempt_to_damage_Linux();
***** disable_Netscape();
***** disable_RealPlayer();
***** disable_Lotus_Products();
***** hang_system();
***** } //if
*** write_something(anything);
*** display_copyright_message() ;
*** do_nothing_loop();
*** do_some_stuff();
*** if (still_not_crashed)
*** {
*** display_copyright_message();
*** do_nothing_loop();
*** basically_run_windows_31();
*** do_nothing_loop();*** }
// if
* } //while
* if (detect_cache())
*** disable_cache();
* if (fast_cpu())
*** {
*** set_wait_states(lots);
*** set_mouse(speed,very_slow);
*** set_mouse(action,jumpy);
*** set_mouse(reaction,sometimes);
*** } //if
* /* printf("Welcome to Windows 3.1");*** */*
/* printf("Welcome to Windows 3.11");** */*
/* printf("Welcome to Windows 95");**** */*
/* printf("Welcome to Windows NT 3.0"); */*
/* printf("Welcome to Windows 98");**** */*
/* printf("Welcome to Windows NT 4.0"); */
* printf("Welcome to Windows 2000");
* if (system_ok())
*** crash(to_dos_prompt)
* else
*** system_memory = open
("a:\swp0001.swp",O_CREATE);
* while(something)***
{
*** sleep(5);
*** get_user_input();
*** sleep(5);
*** act_on_user_input();
*** sleep(5);
*** } // while* create_general_protection_fault();
} // main
#include "win31.h"
#include "win95.h"
#include "win98.h"
#include "workst~1.h"
#include "evenmore.h"
#include "oldstuff.h"
#include "billrulz.h"
#include "monopoly.h"
#include "backdoor.h"
#define INSTALL = HARD
char make_prog_look_big(16000000);
void main()
{
* while(!CRASHED)
* {
*** display_copyright_message();
*** display_bill_rules_message();
*** do_nothing_loop();
*** if (first_time_installation)
***** {
***** make_100_megabyte_swapfile();
***** do_nothing_loop();
***** totally_screw_up_HPFS_file_system();
***** search_and_destroy_the_rest_of-OS2();
***** make_futile_attempt_to_damage_Linux();
***** disable_Netscape();
***** disable_RealPlayer();
***** disable_Lotus_Products();
***** hang_system();
***** } //if
*** write_something(anything);
*** display_copyright_message() ;
*** do_nothing_loop();
*** do_some_stuff();
*** if (still_not_crashed)
*** {
*** display_copyright_message();
*** do_nothing_loop();
*** basically_run_windows_31();
*** do_nothing_loop();*** }
// if
* } //while
* if (detect_cache())
*** disable_cache();
* if (fast_cpu())
*** {
*** set_wait_states(lots);
*** set_mouse(speed,very_slow);
*** set_mouse(action,jumpy);
*** set_mouse(reaction,sometimes);
*** } //if
* /* printf("Welcome to Windows 3.1");*** */*
/* printf("Welcome to Windows 3.11");** */*
/* printf("Welcome to Windows 95");**** */*
/* printf("Welcome to Windows NT 3.0"); */*
/* printf("Welcome to Windows 98");**** */*
/* printf("Welcome to Windows NT 4.0"); */
* printf("Welcome to Windows 2000");
* if (system_ok())
*** crash(to_dos_prompt)
* else
*** system_memory = open
("a:\swp0001.swp",O_CREATE);
* while(something)***
{
*** sleep(5);
*** get_user_input();
*** sleep(5);
*** act_on_user_input();
*** sleep(5);
*** } // while* create_general_protection_fault();
} // main
Web ByPass Tutorial
In this tutorial I'll be showing you how to bypass a filtered network just by following some simple steps. Instead of using a proxy server that uses non-standard ports, I'll be showing you another expolit in an easier way. We'll use the expolit found in the URL mechanism itself. The ideas works as follows:
Converting the URL to an IP address and then to its binary representation or equivalent. This kind of exploit can be used commonly on Mozilla and Netscape. Enjoy bypassing websites at your college, though I don't hold any reponsibility on how you tend to use this information whatsoever.
Use at your own risk !!!
Keep in mind that there are two kinds of filtered network. There is the software and hardware side. In this tutorial we'll be introduing the software side of them.
Step 1: Get the IP address for the web site you need to bypass.
For example, undergroundsystems (http://www.undergroundsystems.org/) blocked in Web-content filtering software has this IP address: 72.29.78.187
I obtained the web domain IP address by pinging the site in command prompt console.
Step 2: Convert each individual number in the IP address to an eight-digit binary number.
Note: Numbers having fewer than eight digits in their binary form must be padded with leading zeros to fill in the missing digits. For example, the binary number 1 is padded to 00000001 by adding seven zeros before the number one.
Each IP address that uses IPv4, is a 32 bit binary number, therefore 4 bytes in total. So we need to convert each quad dotted binary number in the IP address to its binary number.
For each number:
72 = 01001000
29 = 00011101
78 = 01001110
187 = 10111011
The windows Calculator can automatically convert numbers from decimal to binary notation:
i. Choose View -> Scientific.
ii. Click the Dec option button.
iii. Enter the number in decimal value.
iv. Click the Bin option button to show the number in binary format.
Step 3: Assemble or group the four 8 digit binary numbers into one 32-digit binary number.
01001000000111010100111010111011
Note: Don't add the binary numbers. Just organize them in the same order as the original IP address without the separating periods.
Step 4: Convert the 32-digit binary number to a decimal number.
For example, the 32-digit binary number 01001000000111010100111010111011 is equal to the decimal number 1209880251.
The decimal number doesn't need to be padded to a specific length.
Step 5: Plug the decimal number into the Web browser's address field, like this:
http://72.29.78.187/
Viola, the Web Page loads easy as pie!
Note: The preceding steps will not bypass URL's in Internet Explorer (though in some cases it still works).
<<-- Countermeasures -->>
If the bypassing of certain Web-content filters is an issue for your network, ask your content-filtering vendor if it has a solution for it :p
Tutorial written by DarkSolo ,
Happy Hacking
Converting the URL to an IP address and then to its binary representation or equivalent. This kind of exploit can be used commonly on Mozilla and Netscape. Enjoy bypassing websites at your college, though I don't hold any reponsibility on how you tend to use this information whatsoever.
Use at your own risk !!!
Keep in mind that there are two kinds of filtered network. There is the software and hardware side. In this tutorial we'll be introduing the software side of them.
Step 1: Get the IP address for the web site you need to bypass.
For example, undergroundsystems (http://www.undergroundsystems.org/) blocked in Web-content filtering software has this IP address: 72.29.78.187
I obtained the web domain IP address by pinging the site in command prompt console.
Step 2: Convert each individual number in the IP address to an eight-digit binary number.
Note: Numbers having fewer than eight digits in their binary form must be padded with leading zeros to fill in the missing digits. For example, the binary number 1 is padded to 00000001 by adding seven zeros before the number one.
Each IP address that uses IPv4, is a 32 bit binary number, therefore 4 bytes in total. So we need to convert each quad dotted binary number in the IP address to its binary number.
For each number:
72 = 01001000
29 = 00011101
78 = 01001110
187 = 10111011
The windows Calculator can automatically convert numbers from decimal to binary notation:
i. Choose View -> Scientific.
ii. Click the Dec option button.
iii. Enter the number in decimal value.
iv. Click the Bin option button to show the number in binary format.
Step 3: Assemble or group the four 8 digit binary numbers into one 32-digit binary number.
01001000000111010100111010111011
Note: Don't add the binary numbers. Just organize them in the same order as the original IP address without the separating periods.
Step 4: Convert the 32-digit binary number to a decimal number.
For example, the 32-digit binary number 01001000000111010100111010111011 is equal to the decimal number 1209880251.
The decimal number doesn't need to be padded to a specific length.
Step 5: Plug the decimal number into the Web browser's address field, like this:
http://72.29.78.187/
Viola, the Web Page loads easy as pie!
Note: The preceding steps will not bypass URL's in Internet Explorer (though in some cases it still works).
<<-- Countermeasures -->>
If the bypassing of certain Web-content filters is an issue for your network, ask your content-filtering vendor if it has a solution for it :p
Tutorial written by DarkSolo ,
Happy Hacking
Hackers Digest
<< -- Hackers and Crackers -- >>
Hacking has been practiced for more than 100 years. In the 1870's teenagers used to twitter with Phone Systems. Below you'll find how busy these hackers were in the past 35 years.
Hackers come with different culture and believes. They can be grouped with a given colour associated to them. There are various reasons why they hack. Most of them are because they are facinated about computers and technology, others hack for fun, money, politics etc.
What is a Hacker?
A hacker is someone who extends the ability of an object into various measures. Back in the 80's video games where played on a TV set where you had a glimmer pointer orbiting in a circular motion and the hacker used to extend (cheat) describing how many different methods can be used in order for him to win the game.
What is a Cracker?
A cracker is someone who breaks into computer systems normally over networks normally for money or by taking the challenge.
<< -- Magic -- >>
What has Magic got to imply with Hacking?
Hacking is exactly like Magic. Magicians perform magic tricks and get your attention to distract you from noticing what is happening from the background view. If you knew the trick already, it will turn it into divulge. Hacking is same thing. You learn a trick of the trade and until you share your hacking skills and exploits with other people, they won't know how you performed the action.
You see various kinds of Magic as with playing cards, cutting a woman into half etc. You know that this can't be true and that there is a trick in some way or another. But because you don't know what the trick is behind the idea, it is called "Magic".
Hackers come in various different colours such as white, black, grey. They can change colour as a chameleon and hide their identity by covering their face with a mask and being disguised.
What is a White Hat Hacker?
A white hat hacker is someone who hacks into computers systems for a positive intention. He works hand in hand with the system adminsitrators trying to fix holes and attach network patches and also installing vendor's updates.
What is a Black Hat Hacker?
A black hat hacker is someone who hacks into computer systems without the intention of the victim. He normally hacks at night and during after work hours to try and hide identity as much as possible. He is the hacker who performs malicious attacks and deface websites with his own will.
What is a Grey Hat Hacker?
A grey hat hacker is someone who can't be recognized whether it's black or white. He tends to change colour according to the circumstances needed.
What is a Script Kiddie?
A Script Kiddie is someone who is unknowledgable about how computers work and they tend to use others people's tools to gain access to a system or deface a website by posting explicit content on it.
What is an Ethical Hacker?
An ethical hacker is someone who hacks into a system for good purposes such as to delve into a system for security holes and threats. These are normally the white hats who want to patch the system and expose bugs and new holes. They will contribute with adminsitrators and guide them on how they can secure these holes and make their environment more safer.
Hackers often hold conferences and a well known one is "DefCon". It is held in Los Angeles, where hackers meet and share ideas and thoughts.
There is also a hackers magazine called "Phrack" and "2600" that can be found on the web for free of charge.
The hacker code is what describes a hacker himself. You can call it the hacker code or the hacker manifesto.
<<-- Hacker Celebreties -->>
Kevin David Mitnick
Mitnick used his ability on a tecnique called "Social Engineering" where he managed to get access to incorporate systems and high firms such as IBM and Nokia. David was keen about Magic so that he spent hours in a Magic shop trying to figure out how tricks were performed. Then later on while in high school he met a friend who was interested in Phone Phreaking. Him and Mitnick
made up and began sharing there ideas together. He was first arrested in 1988 and sent to trail in 1995. He was sentented to at least five years in jail and was harsly treated using his stay there in federal Prison. He couldn't speak to anyone for quite a long time, until his case was notified and withdrew all charges in 2001. Annoucements and shotouts where displayed on billboards
and stickers with the words "FREE KEVIN" while being in custody.
He has publisehed two notorious books "The Art of Deception" and "The Art of Intrusion" which basically talks about Social Engineering and explaining how to manipulate the humans mind.
John Draper
Draper well known as "Caption Crunch" was into Phone Phreaking which is basically playing around with phone lines and telephone networks. He used to make long distance calls for free without being traced such as doing it from an outside pay phone. Long time ago telephone systems used to work in a more different way than today. If you wanted to phone someone, you had to call the telephone provider first and then they will direct your call to the desired party at the other end. A freqency of tones where wistled through the line making the call pass through. There were various persons who used to make an exact sound by blowing whisps from their mouth and creating an original tone. The tone used to be a 2600Hz tone.
Later on, a wistle with this tone was given out with every packet of cerial bought as a tribute to the occasion. These types of people such as Draper can minipulate a PBX system and do what they desire such as forwarding telephone calls.
Robert Morris
Morris was known for the Morris worm a computer virus that caused various damages to the computers in 1988. It was intentially programmed to test on UNIX systems. Morris was a student from Bell labs and intentially introduced this virus that first occured in the Phillipines.
The worm damages around 6000 networked systems, jamming Govenment and University Systems. Morris was fined $10,000 and sentenced to three years probation.
That's all for now, until next time,
DarkSolo
Hacking has been practiced for more than 100 years. In the 1870's teenagers used to twitter with Phone Systems. Below you'll find how busy these hackers were in the past 35 years.
Hackers come with different culture and believes. They can be grouped with a given colour associated to them. There are various reasons why they hack. Most of them are because they are facinated about computers and technology, others hack for fun, money, politics etc.
What is a Hacker?
A hacker is someone who extends the ability of an object into various measures. Back in the 80's video games where played on a TV set where you had a glimmer pointer orbiting in a circular motion and the hacker used to extend (cheat) describing how many different methods can be used in order for him to win the game.
What is a Cracker?
A cracker is someone who breaks into computer systems normally over networks normally for money or by taking the challenge.
<< -- Magic -- >>
What has Magic got to imply with Hacking?
Hacking is exactly like Magic. Magicians perform magic tricks and get your attention to distract you from noticing what is happening from the background view. If you knew the trick already, it will turn it into divulge. Hacking is same thing. You learn a trick of the trade and until you share your hacking skills and exploits with other people, they won't know how you performed the action.
You see various kinds of Magic as with playing cards, cutting a woman into half etc. You know that this can't be true and that there is a trick in some way or another. But because you don't know what the trick is behind the idea, it is called "Magic".
Hackers come in various different colours such as white, black, grey. They can change colour as a chameleon and hide their identity by covering their face with a mask and being disguised.
What is a White Hat Hacker?
A white hat hacker is someone who hacks into computers systems for a positive intention. He works hand in hand with the system adminsitrators trying to fix holes and attach network patches and also installing vendor's updates.
What is a Black Hat Hacker?
A black hat hacker is someone who hacks into computer systems without the intention of the victim. He normally hacks at night and during after work hours to try and hide identity as much as possible. He is the hacker who performs malicious attacks and deface websites with his own will.
What is a Grey Hat Hacker?
A grey hat hacker is someone who can't be recognized whether it's black or white. He tends to change colour according to the circumstances needed.
What is a Script Kiddie?
A Script Kiddie is someone who is unknowledgable about how computers work and they tend to use others people's tools to gain access to a system or deface a website by posting explicit content on it.
What is an Ethical Hacker?
An ethical hacker is someone who hacks into a system for good purposes such as to delve into a system for security holes and threats. These are normally the white hats who want to patch the system and expose bugs and new holes. They will contribute with adminsitrators and guide them on how they can secure these holes and make their environment more safer.
Hackers often hold conferences and a well known one is "DefCon". It is held in Los Angeles, where hackers meet and share ideas and thoughts.
There is also a hackers magazine called "Phrack" and "2600" that can be found on the web for free of charge.
The hacker code is what describes a hacker himself. You can call it the hacker code or the hacker manifesto.
<<-- Hacker Celebreties -->>
Kevin David Mitnick
Mitnick used his ability on a tecnique called "Social Engineering" where he managed to get access to incorporate systems and high firms such as IBM and Nokia. David was keen about Magic so that he spent hours in a Magic shop trying to figure out how tricks were performed. Then later on while in high school he met a friend who was interested in Phone Phreaking. Him and Mitnick
made up and began sharing there ideas together. He was first arrested in 1988 and sent to trail in 1995. He was sentented to at least five years in jail and was harsly treated using his stay there in federal Prison. He couldn't speak to anyone for quite a long time, until his case was notified and withdrew all charges in 2001. Annoucements and shotouts where displayed on billboards
and stickers with the words "FREE KEVIN" while being in custody.
He has publisehed two notorious books "The Art of Deception" and "The Art of Intrusion" which basically talks about Social Engineering and explaining how to manipulate the humans mind.
John Draper
Draper well known as "Caption Crunch" was into Phone Phreaking which is basically playing around with phone lines and telephone networks. He used to make long distance calls for free without being traced such as doing it from an outside pay phone. Long time ago telephone systems used to work in a more different way than today. If you wanted to phone someone, you had to call the telephone provider first and then they will direct your call to the desired party at the other end. A freqency of tones where wistled through the line making the call pass through. There were various persons who used to make an exact sound by blowing whisps from their mouth and creating an original tone. The tone used to be a 2600Hz tone.
Later on, a wistle with this tone was given out with every packet of cerial bought as a tribute to the occasion. These types of people such as Draper can minipulate a PBX system and do what they desire such as forwarding telephone calls.
Robert Morris
Morris was known for the Morris worm a computer virus that caused various damages to the computers in 1988. It was intentially programmed to test on UNIX systems. Morris was a student from Bell labs and intentially introduced this virus that first occured in the Phillipines.
The worm damages around 6000 networked systems, jamming Govenment and University Systems. Morris was fined $10,000 and sentenced to three years probation.
That's all for now, until next time,
DarkSolo
Thursday, December 18, 2008
Networking1: Network Access Methods Tutorial
In this tutorial we will be discussing network error collision concepts and how to be avoided. When sharing peripherals on a network such as Network Printers, Files and Folders etc, errors may occur. Therefore we need a method to govern the whole network infrastructure. This is called "Network Access Method" and it will determine which PC can have access to the shared medium.
Each machine connected to a network is called a "node". The access method embedded in the NIC (network interface card) takes control of the transfer of data across the network.
There are various methods to take care of data transmission errors in the mechanism itself such as CRC32 (Cyclic Redundancy Check). Basically, it checks and compares the data traveled to the other end, if it's valid and completed. If this fails, it will resend another transmission.
So, the methods that we will be discussing are CSMA/CD, CSMA/CA, Token Ring Passing, FDDI.
What is CSMA/CD?
CSMA/CD stands for "Carrier Sense Multiple Access / Collision Detection" and its purpose is to check whether the network has an available slot to start the passing data. It waits and listens until there is space for the data to be traveled along the
medium. This technique doesn't stop collisions from happening, but it helps. Makes use of 802.3.
What is CSMA/CA?
CSMA/CA stands for "Carrier Sense Multiple Access / Collision Avoidance" and its purpose is to avoid collision by sending Warning messages before sending the data itself. Data may not occur, but warning messages do. So it's still not a reliable method to relay on. Makes use of 802.3.
What is Token Ring Passing?
This is basically the new method designed by IBM, introduced in the 1990's and yes you've guess it. It works by sending a token around a completed electronic virtual ring. Let me demonstrate on how it works. Let's say there are four available computers on a network topology which are PC1, PC2, PC3 and PC4. Now, PC2 wants to transmit a message packet to PC4. The packet leaving PC2 will need to pass to PC3 and then forwarded to PC4 in a circular movement. This will make the token set to flag "busy". As PC4 has completed receiving the data needed it will eventually send the packet header (message frame) back to PC2. Then the packet is set to "idle" state and will wait for another PC that need to transmit data across the network. A break in the network cable will result in network failure. Makes use of 802.5.
What is FDDI?
FDDI stands for "Fibre Distributed Data Interface" and it consists on two rings made from Optical Fibre. These rings are placed in an opposite direction of each other. The first ring is called the primary ring whilst the other is called the secondary ring. As you start transmitting data and the circuit gets broken, it automatically jumps on the second ring.
An advantage over the Token Ring Topology is that with FDDI you can set priorities. For example you can set priority on a networked printer or the server that will make it respond to requests from clients very quickly.
The standardisation for referring to the Ethernet protocol is called "IEEE 802.3". IEEE stands for "(Institute of Electrical and Electronics Engineers, Inc)"
Ethernet is the standard communications protocol built in network hardware and software used for LAN's (Local Area Network).Ethernet can also be wireless where in this case it's "IEEE 802.11".
This was my networking tutorial, until then
DarkSolo
Each machine connected to a network is called a "node". The access method embedded in the NIC (network interface card) takes control of the transfer of data across the network.
There are various methods to take care of data transmission errors in the mechanism itself such as CRC32 (Cyclic Redundancy Check). Basically, it checks and compares the data traveled to the other end, if it's valid and completed. If this fails, it will resend another transmission.
So, the methods that we will be discussing are CSMA/CD, CSMA/CA, Token Ring Passing, FDDI.
What is CSMA/CD?
CSMA/CD stands for "Carrier Sense Multiple Access / Collision Detection" and its purpose is to check whether the network has an available slot to start the passing data. It waits and listens until there is space for the data to be traveled along the
medium. This technique doesn't stop collisions from happening, but it helps. Makes use of 802.3.
What is CSMA/CA?
CSMA/CA stands for "Carrier Sense Multiple Access / Collision Avoidance" and its purpose is to avoid collision by sending Warning messages before sending the data itself. Data may not occur, but warning messages do. So it's still not a reliable method to relay on. Makes use of 802.3.
What is Token Ring Passing?
This is basically the new method designed by IBM, introduced in the 1990's and yes you've guess it. It works by sending a token around a completed electronic virtual ring. Let me demonstrate on how it works. Let's say there are four available computers on a network topology which are PC1, PC2, PC3 and PC4. Now, PC2 wants to transmit a message packet to PC4. The packet leaving PC2 will need to pass to PC3 and then forwarded to PC4 in a circular movement. This will make the token set to flag "busy". As PC4 has completed receiving the data needed it will eventually send the packet header (message frame) back to PC2. Then the packet is set to "idle" state and will wait for another PC that need to transmit data across the network. A break in the network cable will result in network failure. Makes use of 802.5.
What is FDDI?
FDDI stands for "Fibre Distributed Data Interface" and it consists on two rings made from Optical Fibre. These rings are placed in an opposite direction of each other. The first ring is called the primary ring whilst the other is called the secondary ring. As you start transmitting data and the circuit gets broken, it automatically jumps on the second ring.
An advantage over the Token Ring Topology is that with FDDI you can set priorities. For example you can set priority on a networked printer or the server that will make it respond to requests from clients very quickly.
The standardisation for referring to the Ethernet protocol is called "IEEE 802.3". IEEE stands for "(Institute of Electrical and Electronics Engineers, Inc)"
Ethernet is the standard communications protocol built in network hardware and software used for LAN's (Local Area Network).Ethernet can also be wireless where in this case it's "IEEE 802.11".
This was my networking tutorial, until then
DarkSolo
Tuesday, December 9, 2008
My potential IOCCC entry...
Let's get this blog rolling... Here's a piece of code I just wrote with the goal of obfuscating it wildly:
#include <iostream>
int i;main(){for (;i<13\
;++i){printf("%c",((("$2667\02\
6\020;7962\020£\013@\015%\""[i]%60)*2)+(i["\0\1\0\0\1\
\0\0\1\1\0\0\0\1\1\0\0\0\1\1\1\0\
\1\1\0\0\0\1\0\1\1\1\1\0\0\1\0\0\
"]?1:0)));}}///0/0/0/0/1/0/exit(0);}
It prints "Hello, world!".
Basically there are two strings, as the loop iterates they are used to calculate the final letter. I used an ascii table for this. All of these values are <60, so modulo-ing them by 60 does nothing to them. That means, go through string one and find the char with ascii value twice of the current char. If the corresponding entry in string two is true, add one to the result (this is how I fixed it to work with odd numbers as well). The \000 values are octal numbers, which i had to use for the lower numbers like the space and the !.
I don't feel like explaining more now and would much rather drink more beer.
Until next time..
-h3x
#include <iostream>
int i;main(){for (;i<13\
;++i){printf("%c",((("$2667\02\
6\020;7962\020£\013@\015%\""[i]%60)*2)+(i["\0\1\0\0\1\
\0\0\1\1\0\0\0\1\1\0\0\0\1\1\1\0\
\1\1\0\0\0\1\0\1\1\1\1\0\0\1\0\0\
"]?1:0)));}}///0/0/0/0/1/0/exit(0);}
It prints "Hello, world!".
Basically there are two strings, as the loop iterates they are used to calculate the final letter. I used an ascii table for this. All of these values are <60, so modulo-ing them by 60 does nothing to them. That means, go through string one and find the char with ascii value twice of the current char. If the corresponding entry in string two is true, add one to the result (this is how I fixed it to work with odd numbers as well). The \000 values are octal numbers, which i had to use for the lower numbers like the space and the !.
I don't feel like explaining more now and would much rather drink more beer.
Until next time..
-h3x
Hello World
Subscribe to:
Comments (Atom)